Disclosure & Scope. This article documents a pattern of events as experienced by me and supported by contemporaneous records, media artifacts, and observable outcomes. There are numerous constitutional, statutory, and procedural violations associated with these events. Not all violations are listed here. This article focuses on the pattern—how separate acts connect into a self-reinforcing system of escalation, retaliation, and control. Where facts remain disputed, they are presented as such. The objective is transparency and accountability.
repeated harassment, unlawful arrests, property destruction, and sealed-record violations targeting
LeRoy Nellis (HVT – High-Value Target), 2019–2025.
Executive Summary
This is not a story about a single incident. It is a documented pattern of escalation in which allegations became permanent data, data became justification, and justification became repeated abuse—without lawful outcomes.
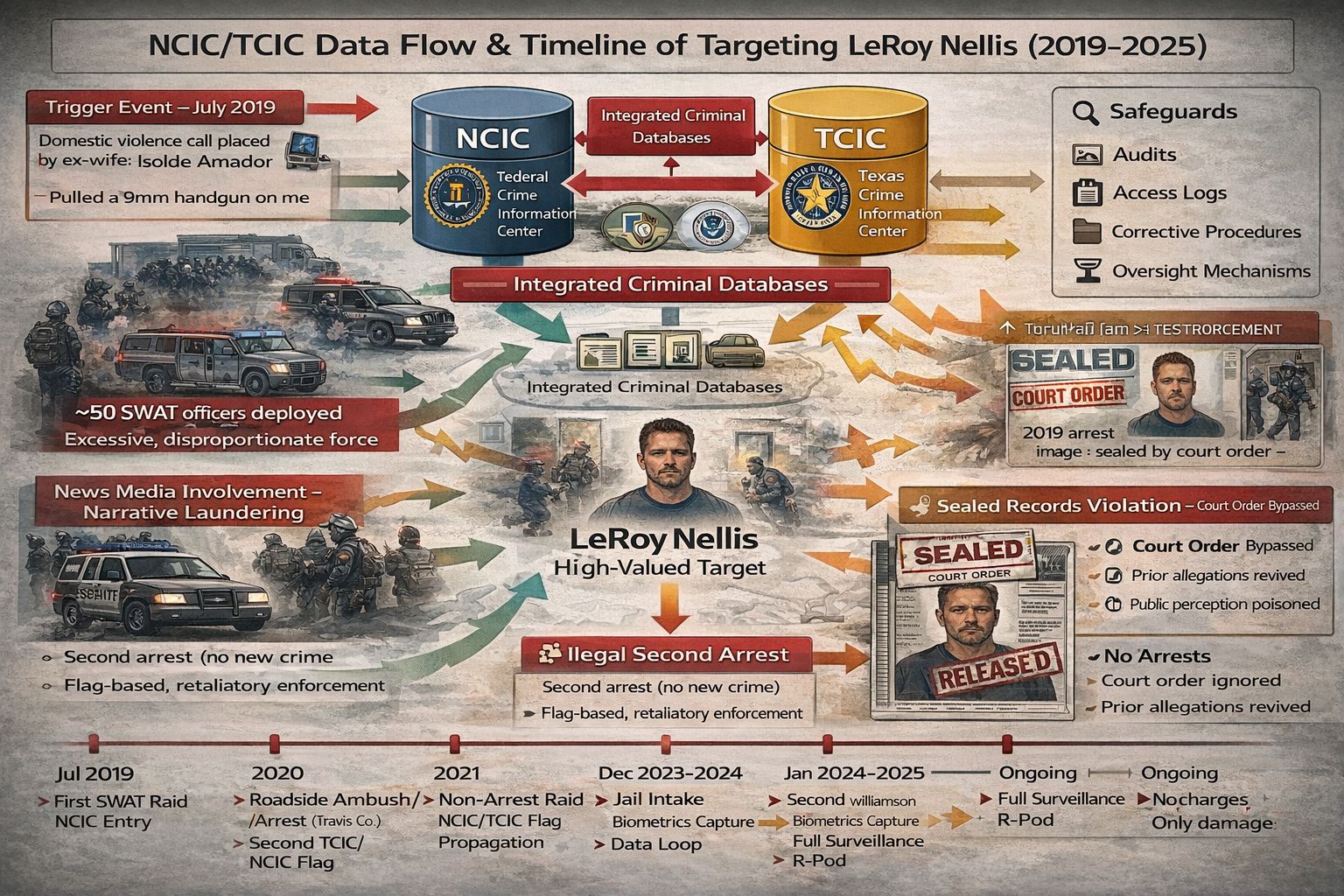
The sequence begins with a domestic incident in 2019, escalates through a militarized response and media amplification, hardens through NCIC and TCIC database propagation, and sustains itself through harassment, arrests without new crimes, property destruction without charges, sealed-record violations, and digital retaliation.
Trigger Event — July 2019
The chain begins with a domestic violence call placed by my ex-wife, Isolde Amador, after she pulled a 9mm handgun on me during a domestic confrontation. Rather than isolating the armed party, law enforcement escalated against me.
This call became the origin node. Every subsequent action traces back to this moment.
Mass SWAT Deployment — Excessive Force
Approximately 50 SWAT officers were deployed. The response was grossly disproportionate. I had committed no crime. The armed party was not treated as the threat.
This militarized escalation established a permanent posture of presumed danger that would be reused to justify future actions.
News Media Involvement — Narrative Laundering
Local and regional news media amplified the law-enforcement narrative generated by the SWAT response. There was no independent verification, no correction of inaccuracies, and no follow-up accountability.
Media exposure did not merely inform the public—it locked in a narrative that would later be reused inside databases, risk assessments, and enforcement decisions.
NCIC / TCIC Database Ingestion
Incident data was ingested into TCIC and propagated into NCIC. Once flags are entered, they persist. They travel across agencies. They become the justification for future escalations.
At this stage, enforcement becomes flag-based rather than evidence-based.
Post-NCIC Digital Surveillance & Retaliation
Immediately following my placement into the NCIC and TCIC databases, I began experiencing coordinated digital surveillance and interference consistent with the use of NCIC- and Securus-associated artificial intelligence systems.
This activity included unauthorized access to, monitoring of, and interference with my personal data, email accounts, websites, cloud services, social media accounts, and digital communications. The conduct occurred without consent, warrant, or lawful authorization and coincided temporally with database propagation and subsequent enforcement actions.
The digital activity was not random. It followed a recognizable pattern of surveillance, intimidation, disruption, and suppression, consistent with retaliation against a designated high-value target. The effect was cumulative: interference with speech, legal preparation, employment opportunities, and public communication.
Digital retaliation functions as an invisible extension of physical enforcement. It leaves fewer visible marks, but it is no less coercive.
HVT Designation and Continuous Harassment
I was effectively treated as an HVT — High-Value Target. This resulted in continuous law-enforcement harassment without new crimes: surveillance, repeated contacts, intimidation, pressure, and digital interference.
The purpose of harassment is not prosecution. It is compliance.
Illegal Second Arrest
A second arrest followed without lawful basis and without new criminal conduct. The arrest relied on prior database flags and narrative rather than evidence.
This arrest further contaminated the databases, reinforcing the same flags that justified the arrest in the first place.
Property Raid and Destruction — No Arrest
Law enforcement raided my mushroom garden and destroyed my property. There was no arrest. No charges. No evidence produced.
This was not enforcement. It was punishment.
Sealed Records Violation — Image Reuse
For a December 2023 arrest, authorities released and republished an image from a 2019 arrest that had been sealed by court order. A sealed record should be legally inaccessible. It was not.
The image was reactivated and redistributed to support a new narrative—reviving prior allegations and poisoning public perception.
Sealed records do not resurface accidentally.
The Feedback Loop
- Domestic call
- Excessive force
- Media amplification
- Database propagation
- Digital surveillance and retaliation
- HVT designation
- Harassment
- Arrests without new crimes
- Property destruction without charges
- Sealed-record violations
Each step reinforces the next. The absence of lawful outcomes does not stop the system—it sustains it.
Why the Absence of Charges Matters
Across raids, arrests, digital surveillance, and destruction of property, the result is consistent: no convictions. No lawful resolutions. Only damage.
When enforcement produces no legal outcomes but continues indefinitely, the objective is not justice. It is control.
Conclusion
This article does not attempt to catalog every violation. There are too many. It documents the architecture of abuse—the way institutions, databases, media, and digital systems combine to create permanent targeting without accountability.
If any authority disputes this account, the remedy is simple:
- Release the use-of-force reports
- Release the database access logs
- Release digital access and monitoring logs
- Release media coordination records
- Release court orders and image-release authorizations
Until then, the pattern speaks for itself.
